Last week,@swaylend ‘s 30m pool $ was locked due to a simple compiler bug, and it took them 4 days to fix it. what exactly happened and any potential threat in the future?
spend 5 minutes reading this post-moterm to find out.

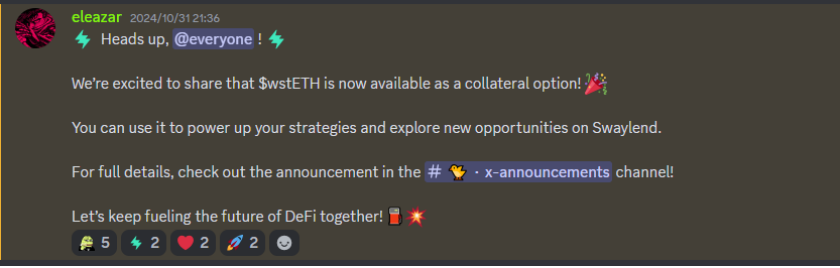
Just 14 minutes later, the first instance of the “revert 123” issue was reported. More users soon faced the same problem.
2. By Nov 1, 05:28, the Swaylend team announced that the issue seemed related to Pyth’s oracle ABI and began troubleshooting.
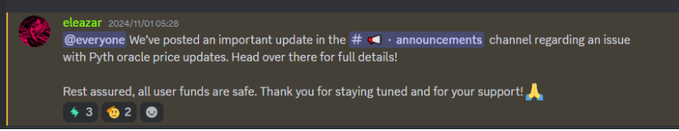
3. On Nov 2, 03:42, Swaylend paused its contracts and deployed a mirror environment on the testnet to investigate further.

4.PR was added to the Sway repository at 06:47 on Nov 2, addressing a memory allocation issue, specifically with dynamic type memory expansion under large input conditions.

5. At 20:32 on Nov 2, the Swaylend team confirmed identifying the core issue and worked actively to resolve it.
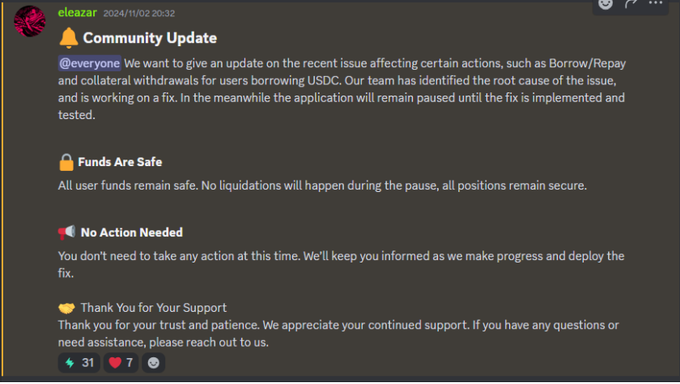
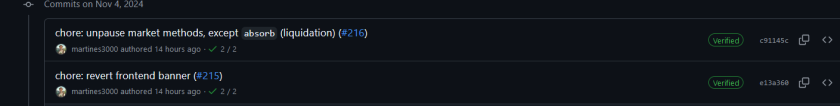
6. Fast forward to Nov 4, 00:12, a new version of the Sway compiler was released, followed by Swaylend’s testnet fix deployment at 01:36.

7. The mainnet fix began at 02:59 on Nov 4, and by 16:31, the issue was resolved, allowing users to withdraw funds without issues.
8.What caused this? The problem stemmed from interactions between Proxy and Market contracts, involving ABI encoding and decoding. The function EncodeBufferAppend had a flaw in handling dynamic memory.

9.Specifically, in grow_if_needed, memory was allocated in 2^n blocks. However, when the required needed_size exceeded 2 * cap, the allocation logic failed, causing data loss.

10. The trigger? wstETH’s addition introduced large data inputs in the PriceDataUpdate, which exceeded the memory allocation limits during withdraw calls.

11. A small quirk explained why some users managed successful withdrawals: cached front-end code in their browsers didn’t reflect updates involving wstETH.
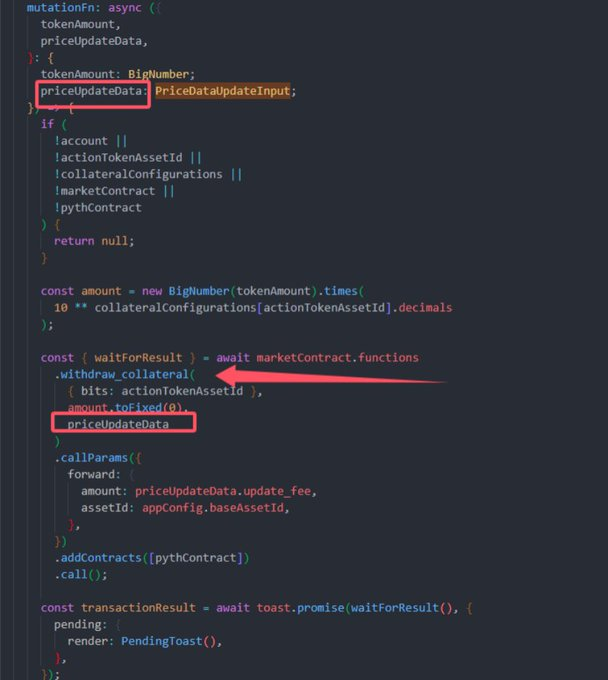
This issue has significant implications for the entire @fuel_network ecosystem, as this compiler vulnerability indicates that all abi encode functions share this flaw, which has the greatest impact on contracts using the Proxy design pattern. Given the nature of this vulnerability, it is relatively difficult to trigger, and most currently functioning contracts are unlikely to encounter this issue in the short term. However, as a leading lending protocol in the Fuel ecosystem, Swaylend experiencing this fund lock-up issue could undermine user trust, potentially leading to a substantial outflow of funds in the short term.
As a leading blockchain security firm, users’ assets safety is our priority. Therefore, we’d continue to provide top-quality audit service for protocols and helps to the users. Do make sure to follow us so you know more about your funds state!